Contents
- How does “buyer” fraud work?
- How fraudsters operate: infrastructure and technological methods
- Main distribution channels
- Example phishing messages
- The role of anti-fraud systems using CFD as an example
- How to prevent “buyer” fraud?
- Case study effective fraud detection based on a real incident
- Summary
- Frequently asked questions
Buyer fraud is one
of the most common methods used to obtain personal data and funds
online. It most often starts with an innocent-looking message, for
example on a sales platform or messaging app, in which the purported
buyer asks the seller to click a link to “receive payment” or
“send the parcel”. The page looks familiar, but it is actually a fake online banking login page.
Schemes of this kind rely on social engineering and a false sense of security, and their consequences can be costly for both users and financial institutions. However, tools such as device fingerprinting and behavioural verification are increasingly used to help detect them.
Let’s take a closer look at how “buyer” fraud works, what techniques cybercriminals use, and how modern systems manage to detect it before funds are lost.
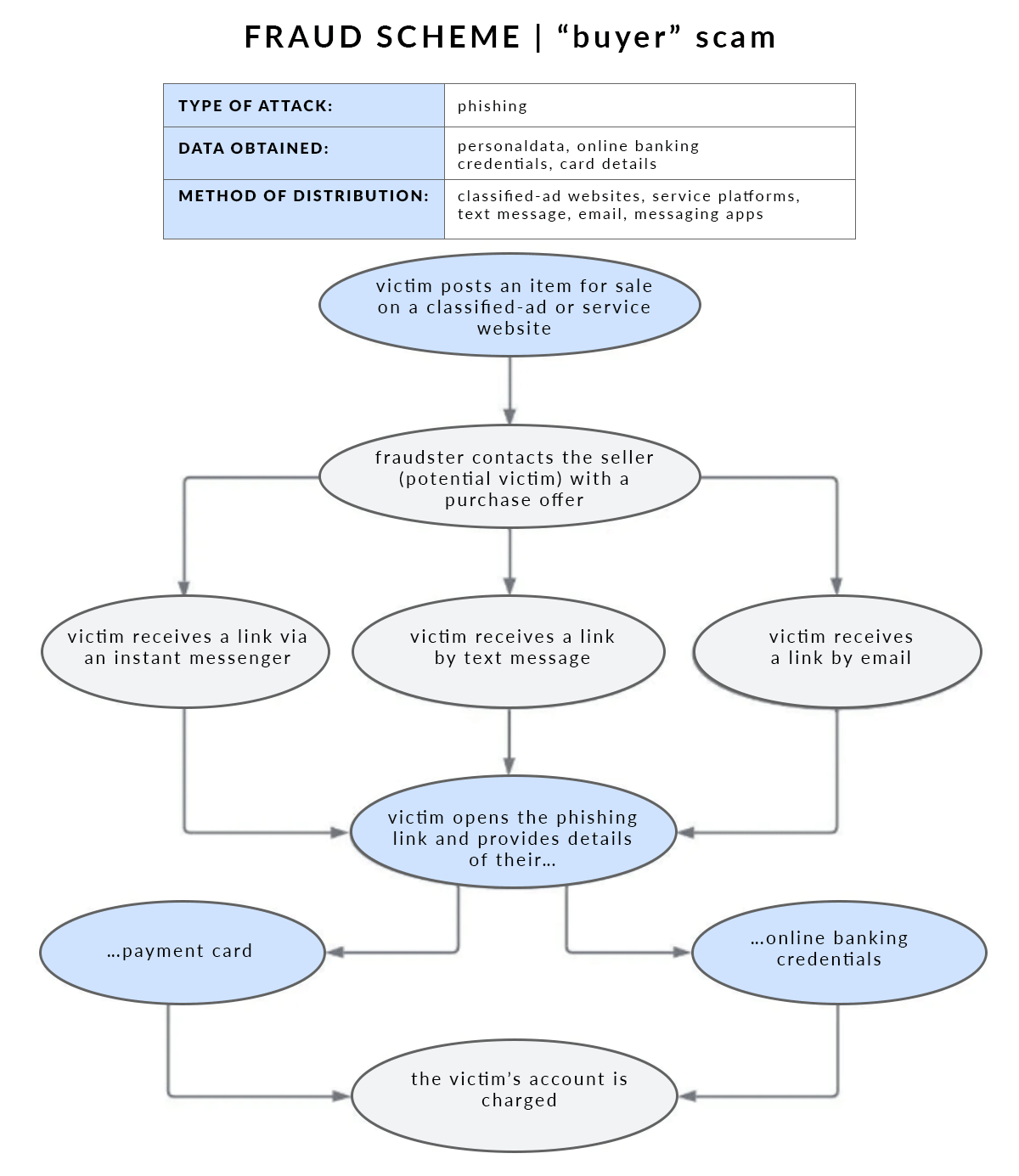
How does “buyer” fraud work?
“Buyer” fraud is an organised and recurring pattern used to fraudulently obtain personal data and money from people selling goods via classified-ad websites. The victim receives a message with a link to a webpage designed to look like a bona fide website, for example a payment system or shipment-confirmation form.
Typical attack scenario:
- Posting of a classified ad by the seller fraudsters monitor new listings on a variety of sales platforms, both in Poland and abroad.
- Contact outside the platform the criminals quickly initiate a conversation via a messaging app or text message and urge the seller to move the exchange off the platform.
- Sending a fake link under the pretext of payment or dispatch, the fraudster sends a link that redirects their target to a fake website.
- Personal data given by the victim the user, unaware of the danger, enters their online-banking login and password or card details into the fraudulent form.
- Logging into the account and attempting to steal funds the fraudsters make immediate use of the captured data.
- Finalisation of the transaction without strong multi-factor authentication (MFA), the fraudster can quickly withdraw funds or modify the account’s settings.
The problem of “buyer” fraud is growing rapidly, as confirmed by the latest reports. In 2023, attacks of this kind accounted for 18% of all phishing incidents connected to auction and retail websites.
The trend was even more worrying the next year. According to the 2024 Orange Polska CERT Report, “buyer” fraud” and other fake payments made up approximately 30% of all recorded phishing attacks.
Buyer scam scheme, Polish Financial Supervision Authority (UKNF). Source: cebrf.knf.gov.pl
How fraudsters operate: infrastructure and technological methods
The effectiveness of “buyer” scams is determined not only by the social-engineering methods used, but also by the extensive technological resources at the fraudsters’ disposal. Criminals use ready-made tools, automation, and fraud-as-a-service solutions, which enable them to operate on a mass scale.
Fake payment gateways and login pages
The fraudster creates a page practically indistinguishable from the genuine site. They use the following to achieve this:
- identical colours, logos and security icons
- forms that mimic the real login page
- URLs with minor modifications
In more advanced cases, live phishing is used. Here data is forwarded to the real website in real time so as not to arouse suspicion.
Spoofing and impersonating trusted sources
Fraudster use a variety of techniques to enhance credibility:
- text messages that look almost identical to messages from authorised suppliers or service providers
- emails sent from addresses deceptively similar to official domains
- contacts may use names such as “Security Department” to inspire trust and create the appearance of authenticity
As a result, even a cautious user may consider such a message authentic.
Automation and fraud-as-a-service campaigns
Fraudsters frequently use ready-made tool-kits available on the dark web. These sets contain the following:
- fake-site generators
- panels for managing links and victims
- bots that automatically monitor new ads
- push alerts when a victim clicks a link
Main distribution channels
Fraudsters have the resources to create realistic phishing websites, fake payment gateways, and to make use of spoofing. However, that alone is not enough to carry out a scam effectively. The key is to reach the victim through the right communication channel one that inspires trust and allows for fast contact outside the control of the classified-ad platform or payment operator.
The distribution channels used most often by fraudsters are:
1. Classified-ad websites
This is where most attacks begin. Fraudsters immediately look for new listings and initiate contact.
Typical features of this stage:
- a message from a “buyer” appears very soon after the classified ad is posted
- the “buyer’s” account often looks realistic it may contain a photo, activity history, and sometimes even a location
- the person making contact urges the seller to switch to a private channel, such as text messages or a messaging app
This allows the fraudster to build an illusion of credibility straight away and control how the conversation unfolds, out of sight of the classified-ad website’s moderation.
2. Messaging apps
Once the conversation has been moved to a messaging app, fraudsters gain far more freedom of action. They take advantage of this to send the target a link to their fake website.
Typical elements of such messages:
- spoofing contact names or phone numbers
- the logo of a well-known courier company, with the link styled to look like a fast-payment system
- shortened links (such as bit.ly) are often used to conceal a suspicious domain name
- sometimes the message imitates an automated transaction system containing an order number, the price, and the website’s name
Thanks to this form of contact, the fraudster can quickly build rapport and minimise their target’s suspicions before they have time to verify the URL or consult somebody.
3. Text messages and emails
Some attacks are carried out via text messages or emails that are practically indistinguishable from system messages sent by well-known companies.
The most common elements of such messages are:
- sender’s name imitating a reputable entity
- brief text informing the recipient of “payment received”, “shipment confirmation required”, or “transaction completed”
- a fabricated link leading to a fake website the domain differs by a single letter or ending (e.g. the address ends with .com instead of .pl)
- additional time pressure, for example: “Link active for only 15 minutes”
Many of these messages appear to be automatically generated, which further lowers the user’s vigilance and increases the attack’s effectiveness. Users should be particularly cautious if a conversation with an unknown buyer quickly moves outside the classified-ad platform and is followed by a request to click an external link.
Example phishing messages
Once the technical infrastructure has been prepared including fake websites, domains, and channels of communication the fraudsters proceed to the key stage of the attack: direct contact with their target. It is the messages sent to the sellers that trigger the “buyer” fraud mechanism.
These messages are often styled as automated notifications from sales platforms, courier companies, or payment systems. Below are some screenshots of actual text messages, emails, and messaging-app conversations that were used in attempts to obtain data or funds fraudulently.
The role of anti-fraud systems using CFD as an example
In the face of increasingly automated and precise attacks by fraudsters, traditional security mechanisms based solely on rules or transaction limits are becoming insufficient. The early detection of suspicious activity, before a transaction is carried out, is becoming crucial. This is where modern anti-fraud platforms, such as Cyber Fraud Detection (CFD), come into play.
How does the CFD anti-fraud system work in the case of “buyer” fraud?
Systems such as CFD analyse multiple layers of data simultaneously, using heuristic models, device fingerprinting, and rule-based logic. The following provides an example of how the system responds:
- The victim receives a message with a link, and logs in to a fake banking website.
- The fraudsters immediately attempt to use the stolen data to log in on the real online banking website.
- CFD analyses the login parameters, including the browser version, operating system, location, and activity timestamp.
- Within a very short time (milliseconds), the system detects device-profile inconsistencies or non-standard behaviour, for example, logging in from another country, a different browser language, or a different screen resolution.
- Based on the anti-fraud rules engine, CFD triggers the appropriate mechanisms that alert analysts and prompt them to verify the suspicious login or transaction.
Example of a rule detected by CFD
In one real-life case, the system generated an alert based on:
- 30 risk rules being triggered
- a mismatch in the device fingerprint between the first and second login (within a few dozen seconds)
- behaviour inconsistent with the user’s pervious patterns (different time of day, different device, different browser language)
- an attempt to access the panel from a new country where the user had never had any previous sessions
Why does this work?
Systems such as CFD combine:
- device fingerprinting identification of the characteristics of the device, the browser, the screen and the system
- risk models which assess the probability of fraud based on the user’s history and comparison with other historical customer data
Their advantage lies in how they operate in real time and at the infrastructure level before the user has time to submit a complaint or notice the loss of funds.
Value for financial institutions and fintechs
Using anti-fraud systems such as CFD enables:
- the system’s rejection of suspicious logins
- the reduction of financial and reputational losses
- the strengthening of user trust thanks to the pro-active approach to security
Importantly, the effectiveness of such systems is not based solely on rigid rules, but on flexible models that learn fraudsters’ behavioural patterns and adjust to changing data-theft techniques. In many cases it is the speed of detection and the appropriate response to the situation that determines whether a customer’s funds are effectively protected.
How to prevent “buyer” fraud?
Modern anti-fraud systems, such as CFD, make it possible to detect attempts at account takeover or logins from suspicious devices in real time. However, this is only one element of an effective defence strategy. In order to meaningfully reduce the risk of customers losing funds, institutions should take coordinated action in key areas such as technology and user education.
Technological safeguards
Effective protection is based on multilayer risk assessment, covering among other things device fingerprinting, geolocation and anomaly detection, as well as dynamic alert rules that respond to current attack vectors. Blocking transactions from suspicious devices or to unusual recipients is also important.
Customer education
An equally important element of fraud prevention is customer education. Financial institutions should conduct regular informational campaigns regarding current fraud schemes, including threats related to fake payment gateways or phishing. Cooperation with classified-ad platforms is also important, in order to jointly warn users against clicking external links or taking steps outside the official ecosystem of a given service.
It is also crucial to promote the principle of limited trust and encourage customers to contact their bank immediately if they have any doubts whatsoever about the authenticity of a message or transaction.
Cooperation between sectors
Cross-sector cooperation plays an important role in combating fraud. The exchange of information between subscribers to anti-fraud solutions, such as PAF (Platforma Antyfraudowa) or CFD (Cyber Fraud Detection), is very important here. It is also important to report malicious domains to registrars and CERT Polska, and to standardise security messages across institutions so that users receive consistent and clear warnings.
Case study effective fraud detection based on a real incident
The security analyst team of a financial institution using the Cyber Fraud Detection (CFD) platform reported a case in which a “buyer” fraud attempt was interrupted before the customer lost any funds. A simplified description of how this incident unfolded is given below.
Fraud scenario
- An individual customer posted a classified ad on a sales platform.
- Several minutes later, the customer received a message on their messaging app informing them of an alleged payment and providing a link for them to collect the money.
- Clicking the link redirected the customer to a webpage imitating the online-banking site. The customer entered their login and password, unknowingly handing their details over to the fraudsters.
CFD system action step by step
- Immediately after the login details were entered, the criminal attempted to log in to the real banking system from another device.
- The CFD platform detected significant differences in the device fingerprints and different IP addresses (customer: Poland; attacker: Russia).
- The system recognised the parallel login attempt within a very short time, which triggered high-risk rules.
- CFD blocked the second login attempt.
Thanks to the system’s rapid reaction, there was no account takeover or loss of funds. The customer was informed of the threat immediately and changed their access details, and the entire situation was recorded as a fraud attempt and forwarded for further analysis.
This case study shows that effective protection against “buyer” fraud does not have to rely solely on a “post factum” response. Properly configured tools can react immediately, before a transaction takes place, thereby protecting the customer’s savings.
Summary
“Buyer” fraud is one of the most common threats faced by users of classified-ad websites and online-banking systems. The attack is based on social engineering, fake payment gateways and spoofing, while the goal of the attack is to steal login details or funds.
Effective protection requires a response before a transaction takes place through behavioural analysis, device fingerprinting and real-time alerts. Designing processes with security in mind is also crucial, as is customer education. Institutions that combine these elements are in a position to significantly reduce the consequences of attacks of this kind.
Frequently asked questions
How can I tell that a payment link sent by a buyer is fake?
Pay attention to the website address it often differs from the genuine address by just a single letter or an unusual domain ending. The absence of an SSL certificate, spelling errors, and a general lack of consistency in the graphics are all warning signs.
Can a bank recover my money after a “buyer” scam?
That depends on the specific case and the moment when it is reported. The sooner you inform the bank, the greater the chances of the funds being blocked or recovered. It is also worth reporting the incident to the police and informing CERT Polska.
How can I increase my security by myself when selling online?
Never click links sent outside the official platform, and never provide your login or card details outside the OLX website or other verified service. If in doubt, consult your bank.
Is it safe to post classified ads on services like Allegro?
Yes, using classified-ad platforms is not dangerous in itself; the danger arises when a fraudster attempts to lure you outside the official system. Always communicate within the platform, and do not click on suspicious links.
What is device fingerprinting and how does it help protect my account?
It is a technology that identifies your device based on its technical characteristics, such as the browser, operating system, and screen. Thanks to this, the system can recognise that someone else is attempting to log in to your account from a completely different device.